Why “Good” Security Programs Still Fail (It’s Not the Technology)
- 4 minutes read - 817 wordsMost security programs fail silently.
Alerts pile up.
Compliance reports pass.
Yet breaches still happen.
It’s a quiet failure that no one celebrates — until it’s too late.
As a CISO or security leader, you’ve likely seen it firsthand: teams overworked, dashboards overflowing, and yet critical risks slip through the cracks.
The tools aren’t broken. The staff isn’t underperforming. The problem is leadership.
Context: The Silent Failures
Security programs are complex ecosystems. They involve monitoring tools, threat intelligence feeds, compliance frameworks, and hundreds of processes. Yet, the programs that look “healthy” on paper often fail in practice.
Why? Alerts get escalated but no decisions are made. Policies are enforced, but no one is accountable. Compliance checks pass, but the organization remains exposed. The problem isn’t technical — it’s organizational.
Lens: Seeing Security Through Leadership
From a leadership perspective, security failures aren’t about misconfigured firewalls or missing patches. They’re about friction, confusion, and unclear ownership.
Consider this scenario: A critical vulnerability is flagged in a core business application. Multiple teams are involved — DevOps, AppSec, IT, and compliance. Without strong leadership, the ticket bounces between teams. Weeks pass. Exploitation occurs. The technology worked. The process existed. But leadership was absent, and that gap created risk.
Anti-Pattern: What Most Security Leaders Get Wrong
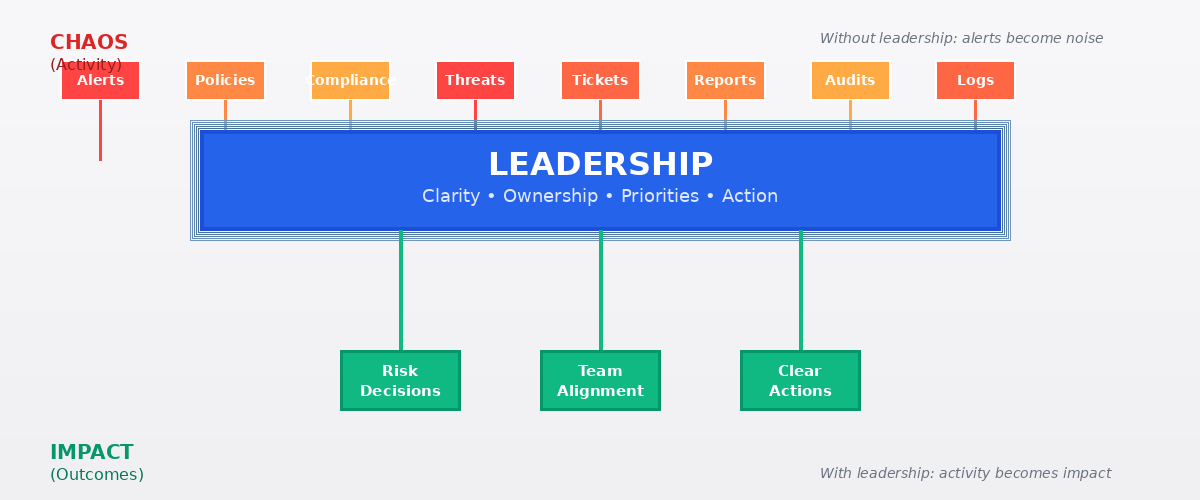
The default response to security gaps is usually technical:
- Buy more tools.
- Enforce stricter policies.
- Hire more staff.
These are activity-focused solutions, not alignment-focused ones. They add layers of complexity without addressing the root cause: a lack of proactive, empowered leadership.
The result? Teams are busy, but outcomes remain poor. Leadership is the lever that turns activity into impact.
Sponsored Insight
Cyber folks and builders: I’ve been moving my automations to Make — a visual way to stitch APIs, webhooks, and cron-like schedules without another brittle script. Think flowchart, but it runs.
What it’s good for:
- OSINT/threat feeds → parse JSON → dedupe → tag severity → alert to Telegram → log to your DB
- Repo/issues → knowledge base → weekly digest
- Creator ops: pull forms, route leads, schedule posts, keep landing pages in sync
Why I like it: routers for branching, retries, rate-limit-friendly pacing, simple secret handling, and clear run logs. Not a silver bullet, but it’s shaved real hours off my week.
Curious? Start tiny (e.g., watch an RSS/CVE feed → alert on keywords) and iterate. Free tier exists. Get Started @ Make.com
This post is brought to you by Make — AI automation you can visually build and orchestrate in real time. Make brings no-code automation and AI agents into one visual-first platform so you can build with speed and scale with control.
Reframe: Leadership Is the Real Security Control
Here’s the insight most organizations miss: security is a team sport, and the team is only as strong as its leadership.
Great leadership reduces friction, clarifies priorities, and ensures that risk decisions are made promptly. It’s not about micromanaging alerts or dashboards — it’s about removing obstacles and creating alignment.
For example:
- Define who owns which risks — and make it visible.
- Create fast-track escalation paths for critical issues.
- Encourage cross-functional collaboration instead of siloed handoffs.
When leaders focus on clarity, ownership, and accountability, security outcomes improve dramatically — often without additional technology spend.
Implication: Why Leadership Gaps Are Dangerous
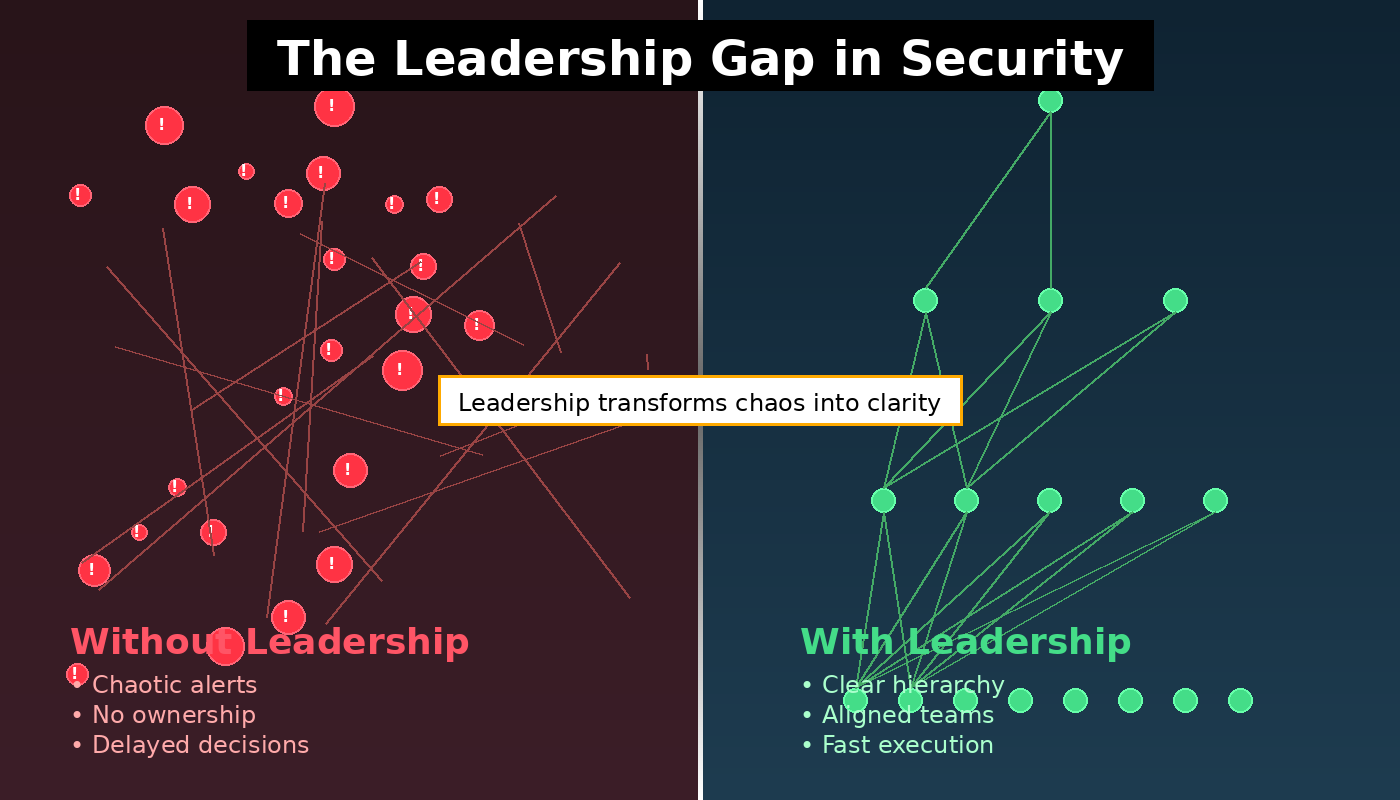
Without leadership, organizations face four key problems:
Delayed Decisions: Critical risk decisions stall, giving attackers a window.
Accumulating Risk: Gaps remain unidentified or unresolved, compounding exposure.
Team Burnout: Staff chase alerts instead of outcomes, leading to fatigue and turnover.
False Compliance: Passing audits feels like security, but it’s only procedural.
Put simply, technology can only enforce rules; leaders enforce priorities.
Takeaway: Leadership as the Ultimate Security Control
If you want to build resilient security programs, stop chasing tools or dashboards first. Start with leadership. Clarity, alignment, and proactive decision-making are the ultimate controls.
- Define clear roles and responsibilities.
- Remove friction between teams.
- Set priorities that align with business risk, not just activity metrics.
Security programs succeed when leaders act like the conductor of an orchestra — ensuring every player knows their part and every note contributes to the mission.
Why This Matters for CISOs
Great security doesn’t happen by accident. It happens when leaders:
- Define priorities clearly.
- Remove organizational friction.
- Elevate their teams to focus on outcomes, not just activity.
Leadership is the control plane. Tools and processes are the instruments. Without one, the other can’t perform.
Premium Resource for Security Leaders
To help you translate this insight into action, check out Cybersecurity Leadership OS — a Notion-based toolkit with over 30 mental models, decision frameworks, and real-world guides designed for CISOs and Deputy CISOs.
- Align your teams faster
- Make better risk decisions
- Elevate your program’s impact
💡 If you found this helpful, learn the thinking that separates leaders from followers
🚀 Supercharge Your Cybersecurity Career with 🔗 CyberSHIELD PRO Membership – Unlock Exclusive Benefits Today!
Stay informed, stay empowered,
CyberSHIELD | CybersecurityOS