Good CISO vs. Bad CISO: The Hidden Mindsets That Make or Break Security Leadership
By Michael Tayo
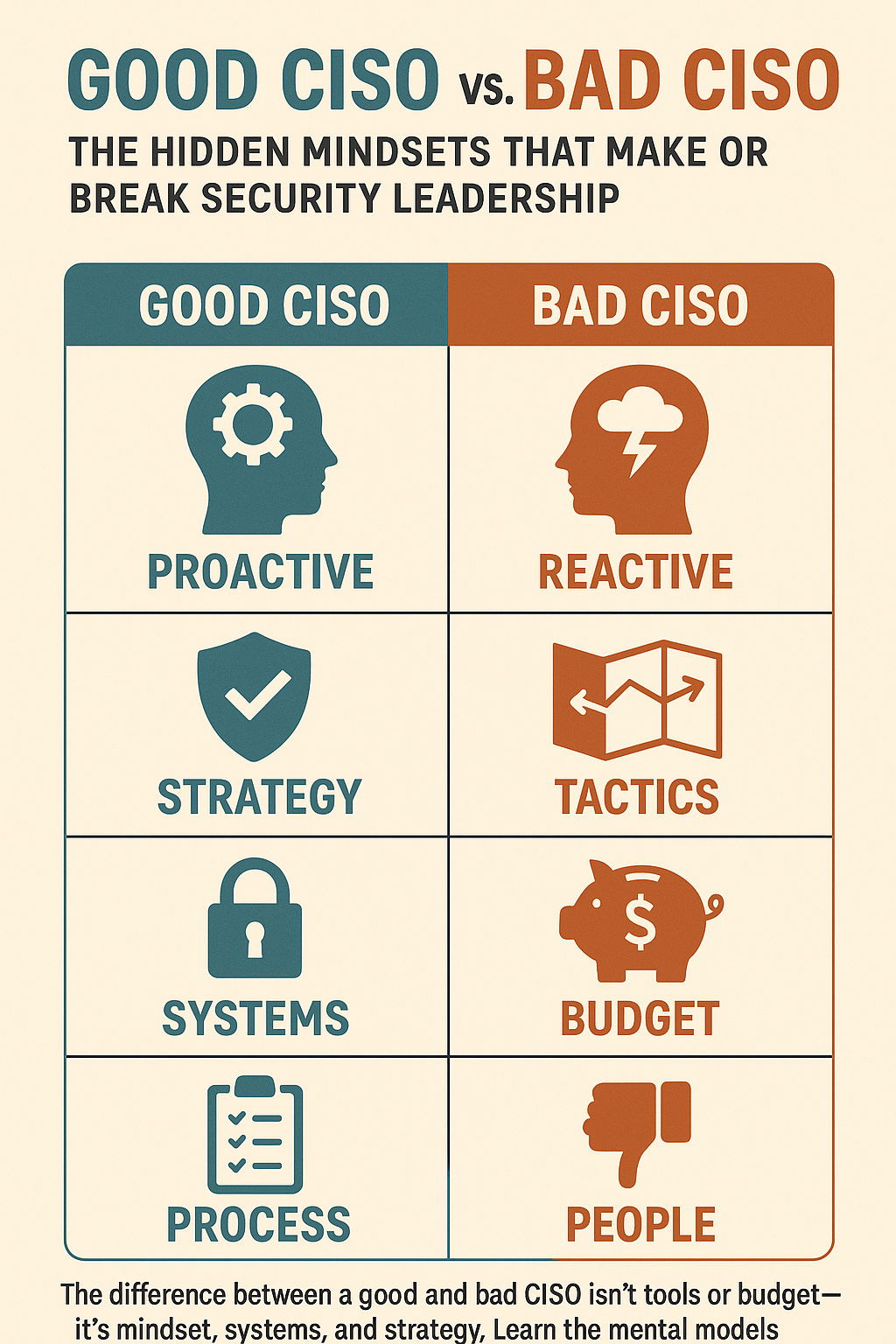
- 3 minutes read - 530 wordsInspired by Phil Venables’ Good CISO / Bad CISO framework, this piece explores the mental models that distinguish effective security leaders from those trapped in reactive cycles.
I’ve spent the past decade working across cloud, application, and enterprise security. I currently serve as an Information Security Lead and Deputy CISO.
My work centers on advising executives on risk, resilience, and security strategy while ensuring that security aligns with broader business priorities.
Along the way, I’ve earned a Master’s degree in Cybersecurity and several industry certifications, but what has mattered most is applying that knowledge to real-world challenges: leading teams, scaling security programs, and building trust with stakeholders.
Beyond my day-to-day role, I mentor, speak, and create resources to help emerging leaders navigate the same path—bridging technical depth with executive-level strategy.
What stands out in Venables’ framework is that many “bad” CISO traits don’t come from a lack of intelligence or effort. They emerge from environments that pull leaders into firefighting mode and strip away the space needed for long-term thinking.
That’s the lens through which I explore these mental models.
Sponsored By
💡 Power your growth with the tools I personally use:
- 🚀 Hypefury — The ultimate tool for growing your audience and automating Twitter threads that actually go viral.
- 🎨 Carrd — Build beautiful, responsive landing pages in minutes. Perfect for portfolios, waitlists, and personal branding.
The Mental Models That Matter

Flywheel vs. Fire Station
- A good CISO builds compounding systems (think AWS’s “security is everyone’s job” model).
- A bad one runs from incident to incident, counting tickets.
Leverage vs. Force
- The best CISOs scale through automation, influence, and culture.
- The worst rely on brute force and more tools.
Hazard + Outrage
Risk isn’t just technical—it’s how stakeholders feel about it. Ignoring perception is how small issues spiral into crises.
Executive Level (Vision & Accountability)
Action Item: Frame board updates around business resilience and trust capital, not just vulnerabilities patched.
- Example: “Our phishing resilience improved by 30%—which directly reduces potential fraud losses by $XM.”
Action Item: Teach boards meta-questions—e.g., “What assumptions are we making about our cloud dependencies?”
Strategic Level (Systems & Scale)
Action Item: Create a security champions network inside engineering—like Atlassian does—so security knowledge compounds instead of bottlenecking in one team.
Action Item: Leverage procurement. Instead of buying another monitoring tool, push SaaS providers to meet higher security baselines. That single act scales security far beyond the org.
Operational Level (Culture & Execution)
Action Item: Build a “bad news travels fast” norm. At one firm I’ve seen, engineers are rewarded for surfacing risky misconfigs early—before they hit production.
Action Item: Document repeatable decisions (risk registers, FAQ playbooks) so teams aren’t reinventing the wheel. This creates durable clarity and reduces cognitive load.
Insight: The real risk is not “Bad CISOs” — it’s organizations that force even good ones into firefighting. Without the right mental models and structures, strategy collapses into tools, excuses, and short-term wins.
So the thought I’ll leave the room with: What systems can we design so that staying strategic isn’t an act of heroism for CISOs, but the default mode of operation?
For the original framework by Phil Venables, see Good CISO / Bad CISO.